How Does GPS Spoofing Work?
Introduction: Why GPS Spoofing Matters More Than Ever
Every time you open Google Maps, call a cab, or track a delivery, you’re relying on the Global Positioning System (GPS) to show the right location. But what if someone could send fake satellite signals that make your device believe it’s somewhere else? That’s exactly the mystery behind the question — “How Does GPS Spoofing Work?”
In simple terms, GPS spoofing is a cyber-attack that manipulates satellite navigation signals to mislead a GPS receiver. By broadcasting counterfeit signals that mimic the real ones, attackers can alter your device’s calculated position or timing data. From personal navigation apps to aircraft, ships, and defense systems, this silent manipulation can create serious disruptions.
What Is GPS Spoofing?
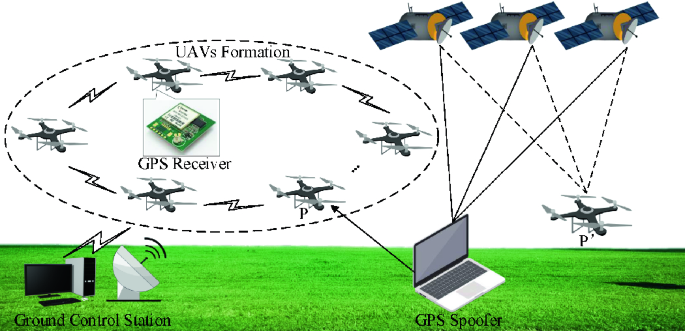
At its core, GPS spoofing is a form of signal deception. It tricks GPS receivers into believing they are at a false location by broadcasting counterfeit GPS signals. Instead of using real satellite transmissions, a GPS spoofer — often a small transmitter or software-defined radio — sends stronger fake signals that override the legitimate ones.
The receiver, unable to tell the difference, calculates its position based on these counterfeit signals. As a result, the system believes it’s somewhere else entirely — perhaps kilometers away from its true coordinates. This false data can cause vehicles, ships, or even smartphones to display inaccurate routes or coordinates.
In simpler terms, GPS spoofing is like giving your phone fake directions from space. It’s a silent, invisible manipulation that can confuse both humans and machines that depend on location accuracy.

How GPS Positioning Works
Before understanding how GPS spoofing works, it helps to know how genuine GPS operates. The Global Positioning System (GPS) relies on a constellation of satellites orbiting Earth. Each satellite continuously transmits a signal containing its position and a precise timestamp. Your GPS receiver (in a car, drone, or smartphone) listens to multiple satellites and calculates how long the signals took to arrive. From that timing information, it determines your position through a process called trilateration.
However, there’s a catch — by the time satellite signals reach Earth, they are extremely weak. Their strength is often less than a tenth of a watt. This weakness makes them vulnerable to interference and manipulation. A nearby gps spoofer device can easily transmit a slightly stronger signal, overpowering the legitimate ones. When that happens, the receiver begins processing the counterfeit data instead of the real signal .
How Does GPS Spoofing Work?
So, how does GPS spoofing work in practice? Let’s break it down step by step.
1. Identifying the Target
An attacker first studies the target — whether it’s a drone, vehicle, or ship — to understand how its GPS receiver processes signals. This step helps determine what kind of spoofing pattern or signal power will be needed to deceive the receiver.
2. Crafting the Fake Signal
Using a gps spoofer device (which can range from specialized transmitters to software-defined radios), the attacker generates counterfeit satellite signals. These signals replicate the exact format of genuine GPS data — including timing, frequency, and satellite identifiers — but they embed false position or timing data.
3. Transmitting the Spoof
The counterfeit signal is broadcast at a slightly higher power level than real satellite signals. Since GPS receivers automatically lock onto the strongest available signal, the fake signals take priority. The receiver, now “tricked,” believes the counterfeit data and recalculates its position based on those values.
4. Maintaining the Illusion
To prevent detection, the attacker gradually shifts the reported GPS location instead of making a sudden jump. This slow drift keeps navigation systems or users unaware that spoofing is occurring. In advanced cases, spoofers synchronize their signals so perfectly that even aircraft autopilots or drones follow the false path smoothly without alarm.
This process allows an attacker to “move” any GPS-based system virtually anywhere on the map — without physically relocating it.
The Tools: What Is a GPS Spoofer Device?
A GPS spoofer device is any tool that can create and transmit fake GPS signals. These can be hardware-based or software-based:
- Hardware spoofers: Small radio transmitters or SDR (software-defined radio) units capable of generating GPS-like signals at a specific frequency. They’re often custom-built or modified from open-source radio projects.
- Software spoofers: Applications that simulate GPS data on smartphones or computers for testing purposes. While legitimate for developers, such software can be misused for location cheating.
Commercially, such devices are restricted, and operating one to deceive others is illegal in most countries. However, researchers may use controlled spoofers in labs to test GPS resilience under ethical and legal conditions.

Real-World Examples of GPS Spoofing
1. Maritime Incidents
One of the most documented effects of GPS spoofing occurs in the maritime industry. Ships near certain strategic regions have reported their GPS showing locations hundreds of kilometers away from their true position. This can cause navigational hazards, route confusion, and port delays.
2. Aviation Concerns
Aircraft depend heavily on satellite navigation for route tracking and landing systems. If a gps spoof affects these systems, it can potentially cause misalignment with flight paths or incorrect altitude readings — leading to serious safety concerns.
3. Rideshare and Delivery Maintenance
Even on a smaller scale, spoofing affects daily life. Drivers or couriers using navigation apps can be rerouted or appear in the wrong areas, resulting in wrong deliveries, false charges, or delayed pickups.
4. Industrial and Military Impacts
Telecommunication towers, energy grids, and defense systems also synchronize operations using GPS time signals. A spoofing attack could create timing errors that ripple through critical infrastructure.
How to Detect GPS Spoofing
While GPS spoofing can be subtle, there are warning signs that can alert users to suspicious activity:
- Sudden Location Jumps: Your device reports a completely different location instantly, without any actual movement.
- Unrealistic Speed Changes: Your app shows you moving impossibly fast or teleporting between points.
- Signal Strength Variations: A stronger-than-usual GPS signal can sometimes indicate a nearby spoofing device.
- Multiple Devices Disagreeing: If two GPS devices in the same area show different coordinates, one may be spoofed.
Monitoring these signs can help detect spoofing early, especially in logistics or fleet systems where location accuracy is mission-critical.
Countermeasures: How to Protect Against GPS Spoofing
While spoofing is difficult to eliminate completely, several defense strategies can reduce the risk.
1. GPS Signal Authentication
Future satellite systems are developing authentication features that allow receivers to verify whether a GPS signal is genuine. This cryptographic validation prevents counterfeit signals from being accepted.
2. Multi-Signal and Sensor Fusion
Systems can use multiple navigation sources — such as inertial measurement units (IMUs), GLONASS, or Galileo — alongside GPS. If one source deviates unexpectedly, the system can cross-verify with others to maintain accuracy.
3. Signal Processing and Detection Algorithms
Advanced receivers analyze characteristics like signal strength, Doppler shift, and timing consistency. Any deviation triggers an alert or rejection of suspect data.
4. Awareness and Operational Protocols
Human awareness remains vital. Training personnel to recognize signs of spoofing and establishing response procedures are critical for large organizations.
5. Digital Security Layers
Even though GPS spoofing is a signal-level threat, having strong device and network security helps protect against broader manipulation. The PDF mentions solutions like McAfee+, which can safeguard personal data and connected devices as an added layer of defense.
Legal and Ethical Aspects
It’s important to understand that using a GPS spoofer maliciously is illegal in most countries. Unauthorized interference with GPS signals can result in fines, equipment confiscation, or imprisonment.
Governments treat GPS as a public utility and national security asset, so tampering with it — even unintentionally — has serious consequences.
That said, there are legitimate research and testing uses. For example, universities or technology firms may conduct controlled spoofing tests inside shielded environments to evaluate the robustness of GPS systems. These tests are crucial for improving global GPS resilience, but must follow ethical and legal standards.
The Future of GPS Spoofing and Counter-Spoofing
Technology is a double-edged sword. As GPS spoofers become more sophisticated, defense technologies also evolve. Researchers are developing next-generation GPS authentication systems, AI-based anomaly detection, and hybrid navigation algorithms that can identify spoofing patterns in real time.
Governments and agencies worldwide are also strengthening legal frameworks and cross-agency coordination to respond quickly to GPS threats.
In the future, GPS receivers might automatically cross-check signals with cloud-based integrity databases or regional terrestrial beacons — making spoofing harder to execute without detection.
Summary: Staying One Step Ahead
GPS spoofing isn’t just a technical curiosity; it’s a growing challenge to global navigation, safety, and security. Understanding how GPS spoofing works helps us prepare better defenses and create awareness among users and organizations.
Let’s recap the key points:
- What is GPS spoofing? It’s the act of transmitting fake GPS signals to mislead receivers about their real location.
- How does GPS spoofing work? Attackers use stronger counterfeit signals to override authentic satellite transmissions, making receivers calculate false positions.
- What tools are used? A GPS spoofer device can be hardware (radio transmitters) or software (signal simulators).
- Why does it matter? It affects everything from smartphone navigation and delivery tracking to aviation and national defense.
- Can it be stopped? Yes, with authentication, multi-signal systems, anomaly detection, and legal controls — though ongoing vigilance is essential.
Final Thoughts
In a world increasingly dependent on precise location data, GPS spoofing poses a silent yet potent risk. Its ability to manipulate trust in navigation systems makes it both fascinating and dangerous. But awareness, innovation, and ethical regulation can keep the GPS ecosystem resilient.
For everyday users, keeping software updated, monitoring device behavior, and understanding the basics of how GPS spoofing works go a long way toward staying safe in the digital skies.

